Originally published September 4, 2021 @ 3:46 pm
I’ve been fiddling with my inotifywatch scripts to make a better “early-warning” system for ransomware detection and realized I needed a more realistic honeypot data structure. Ransomware is getting more clever and is no longer easily fooled by dummy files from /dev/urandom or popular file collections.
This all started early Friday morning, which was my day off. I had an hour to kill and figured that was just enough time to throw together a quick script that would generate a sufficiently realistic data structure to be used for a ransomware honeypot.
Skipping my bicycle ride and pretty much everything else I had planned for that day, sixteen hours later, I was still at it. Talk about going down a rabbit hole…
Here’s a quick rundown of what this script does.
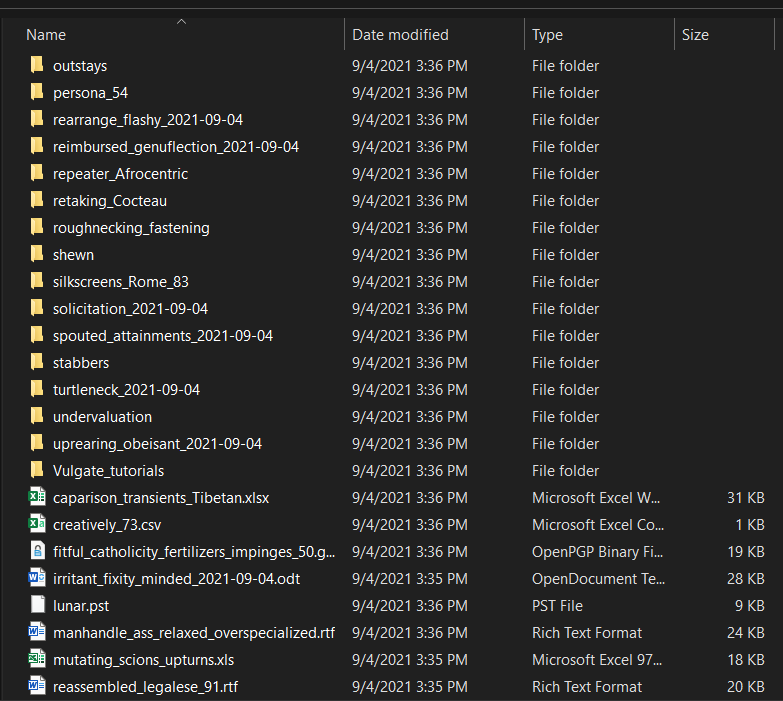
When executed without arguments, the script will generate up to three thousand files of various sizes and common mime types. Filenames are derived from this dictionary file with some random bits added on occasion.
The files are created using fallocate. To make them look a bit more believable, the script will consult this JSON file for the pattern appropriate for that particular mime type. These patterns are used by the file command (libmagic) and other similar utilities (and malware) to identify file types.
The script will dump each file to HEX, replace the first line with the appropriate pattern, and convert the file back to binary. I am still fiddling with the JSON file and the patterns, but it seems to work OK at least for some file types.
Finally, the script will generate a folder structure and randomly move most of the files into those folders.

Experienced Unix/Linux System Administrator with 20-year background in Systems Analysis, Problem Resolution and Engineering Application Support in a large distributed Unix and Windows server environment. Strong problem determination skills. Good knowledge of networking, remote diagnostic techniques, firewalls and network security. Extensive experience with engineering application and database servers, high-availability systems, high-performance computing clusters, and process automation.