Originally published January 17, 2018 @ 10:06 pm
When the SSL Digital Certificate is intercepted and replaced by a device between your browser and the Web site, we call it certificate injection. This method is more commonly used not by hackers, but by corporate IT security utilizing appliances known as SSL sniffers, such as Blue Coat ProxySG or Netronome SSL. These systems are also known as IDS/IPS, or DLP appliances.
To make a long story short, the sniffer receives the Web site’s cert but sends you its own – also a perfectly valid cert that has already been added to the trusted sources on your corporate laptop.
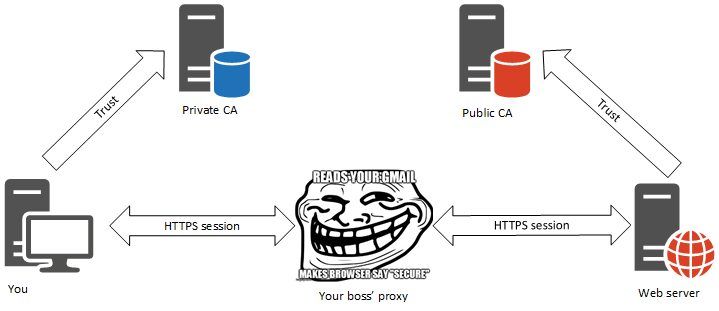
Think of this as the sniffer acting as the Web server as far as your browser is concerned. It is also acting as your browser, as far as the Web server can tell. It’s like FedEx leaving a parcel with a nosy neighbor, who looks inside, then reseals it and hand-delivers it to your door.
Now imagine that you obtain the Web site’s certificate’s fingerprint from your laptop and also from your home computer unaffected by the sniffer because it’s not on your company’s network. The two fingerprints will not match and this is how you will know you’re being screwed.

The small script below does just that: gets the fingerprint directly and then repeats the process via one or more remote proxy servers of your choice. It will tell you if the fingerprints don’t match.
#!/bin/bash
# |
# ___/"\___
# __________/ o \__________
# (I) (G) \___/ (O) (R)
# Igor Os
# igor@comradegeneral.com
# 2018-01-16
#
# ---------------------------------------------------
# Obtain a remote sites SSL fingerprint via localhost
# and compare it to the fingerprintes received via
# remote proxies. This can be useful for identifying
# potential SSL sniffing via certificate injection.
# ---------------------------------------------------
domains="${@}"
if [ -z "${domains}" ]; then echo "Specify domains"; exit 1; fi
rproxies="192.168.122.12 192.168.122.13"
leip="$(curl -s0 -k -q ifconfig.me 2>/dev/null)"
echo "${HOSTNAME} external IP: ${leip}"
for d in ${domains}; do
for rproxy in ${rproxies}; do
lsha="$(openssl s_client -connect ${d}:443 < /dev/null 2>/dev/null | openssl x509 -fingerprint -sha1 -noout -in /dev/stdin | awk -F= '{print $NF}')"
rsha="$(ssh -qt ${rproxy} "openssl s_client -connect ${d}:443 < /dev/null 2>/dev/null | openssl x509 -fingerprint -sha1 -noout -in /dev/stdin" 2>/dev/null | awk -F= '{print $NF}')"
if [ "$(echo "$lsha" | tr -dc '[:print:]' | od -c)" != "$(echo "$rsha" | tr -dc '[:print:]' | od -c)" ]; then
reip="$(ssh -qt ${rproxy} 'curl -s0 -k -q ifconfig.me 2>/dev/null')"
echo "Proxy's external IP: ${reip}"
colordiff <(echo "$lsha" | tr -dc '[:print:]' | od -c) <(echo "$rsha" | tr -dc '[:print:]' | od -c)
else
echo "${d} checks out via ${rproxy}"
fi
done
done

Experienced Unix/Linux System Administrator with 20-year background in Systems Analysis, Problem Resolution and Engineering Application Support in a large distributed Unix and Windows server environment. Strong problem determination skills. Good knowledge of networking, remote diagnostic techniques, firewalls and network security. Extensive experience with engineering application and database servers, high-availability systems, high-performance computing clusters, and process automation.























